We tend to think of cyber attacks happening to banks, or governments, but HR needs to wake up to the fact that we are the keepers of a lot of sensitive data, and we need employees to help us.
“I never thought I would be briefing the President of the United States of America on a bad Seth Rogen movie,” admitted an anonymous Obama staffer at the time.
Yet there they were, in the situation room, summarizing the half-baked plot of a movie that should have been doomed to b-flick oblivion. Instead, even before its release, The Interview became the fulcrum of an international debacle that would bring the US and North Korea to the brink of nuclear war…again.
James Franco stars as a tabloid talk-show host gaining access to the elusive North Korean Supreme Leader, Kim Jong-un, for an interview, and is subsequently recruited by the CIA to assassinate the dictator.
Before the slated premiere in October 2014, the People’s Republic issued a scornful press release, saying that ”making and releasing a movie on a plot to hurt our top-level leadership is the most blatant act of terrorism and war and will absolutely not be tolerated.”
Though threats from this easily goaded nation were hardly taken seriously, Sony PIctures pushed the release date to the end of November, hoping the ire would blow over. But things just got worse.
The Monday before Thanksgiving, when Sony employees attempted to log on to their computers, a grinning skeleton greeted them with a cryptic, if grammatically reprehensible, admonition: “Hacked by #GOP, Warning: We’ve already warned you, and this is just the beginning. We will continue until our requests have been met…”
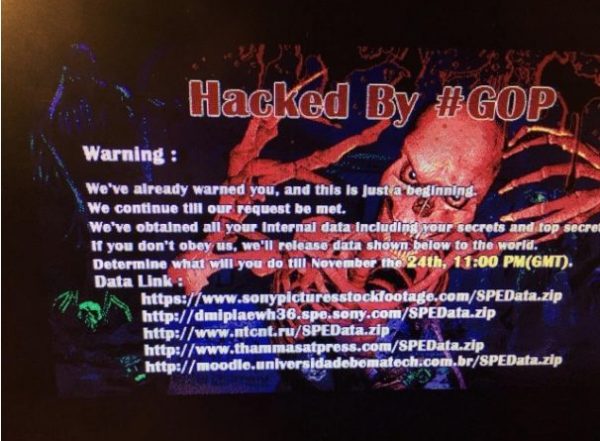
“It was like a bomb went off,” one Sony staffer told Slate.com. “We looked around. We were still alive. So we started doing triage.”
The #GOP, or Guardians of Peace, claimed responsibility, and though the far-east Hermit Kingdom denied direct involvement, they dubbed the attack “righteous”, and ceded the possibility that supporters of the regime were responsible, which brings us back to the White House, where a room full of government officials, including POTUS, were trying to decide: “Is this an act of war?”
If it could be considered as such, the world’s only superpower didn’t retaliate beyond more sanctions to the already sanction-sagging country. Because when it comes to cyber warfare, there’s not much in North Korea to attack. Advanced nations like the US are much more vulnerable. Every smartphone, fitbit, computerized fridge, virtual assistant, navigations system, etc, is another point of entry for nefarious actors, and every day there’s a new way in.
The Sony breach was made possible, in part, by the employees themselves, or more, their lazy passwords – in three cases the password was actually “password” – though the hacker organization made claims, still unsubstantiated, that they had “help from the inside.”
Another insider told Slate of the breach, “some of the worst team players were in HR, because the nature of the hack — leaked Social Security numbers, exposed medical info, a trashed payroll system — meant their department was one of the hardest hit.” And that will likely continue to be the case in future breaches, as HR will always be a hub of sensitive personal data.
Since a future where your average Joe uses a different 12-digit, case-sensitive, alphanumeric password for every online account seems unlikely, the question becomes, “How can we create a cyber-security practice that people will actually follow?”
Because while cyber-security spending is projected to reach $101.6 Billion globally by 2020 (a 38 percent increase from 2016), what’s missing is the grassroots buy-in. For this, we talked to cyber-security expert, Sana’ Rasul – Head of HR Girlfriends, with over a decade of HR experience. She helps businesses make security policies that employees can actually understand, and execute, so your data isn’t just safe “on paper”.
You weren’t always a cyber-security advocate, what made you become interested in this issue?
I was hacked three times in one year! I didn’t know it at the time, but I wasn’t protecting myself. I was getting stuff done on the go – as most people do – and hopping onto any random WIFI. Thankfully, it was only my personal credit card info that was stolen, but it made me think, ‘I use my company credit card all the time, and I use same processes I use for my personal credit card… Oh no.’ So it was a spiral effect, where my personal challenge forced me to look at the way I do business. I wouldn’t want my clients to be compromised, that would be awful!

What mindset should companies have when creating their cyber-security policy?
You have to approach cyber-security as an in-user, The policies you put into place have to make sense for the way people actually work.
So how do you make a policy that your employees will follow?
Be sure to explain your policies in a way that employees will understand. That means examples! Talk to your employees, identify all the scenarios in which they use company technology or access company servers, and make a policy that takes the reality into account. For example, you can’t say ‘no using open-wifi,’ if you also expect workers to be reachable at all times. The reality doesn’t line up with the on-paper policy. A more effective measure would be to provide company portable WIFI routers and require employees to use those secure networks.
Where should HR start?
Handbooks! It may seem antiquated, but handbooks that compile all the need-to-know information for employees can be super helpful, it’s the groundwork for how they will use the technology provided them. Creating a handbook also forces your company to asses the health of its cyber-security, identify potential breaches, and make a plan of action.
What’s the number-one thing companies do wrong?
The most common thing I see are policies that haven’t been updated. We update our computers, we update our phones, we update everything except our policies that influence our use of technology. Companies should be reviewing their guidelines every year. The other thing is, I see policies that are 20 pages, but still don’t manage to get to the way people really work, the reality I talked about before. Be specific about usage and access of company tech and data, and it will make it easier for your employees to execute.
What does a forward-looking cybersecurity policy look like?
You need to be thinking ahead, every time you see a tech innovation, think, ‘what does that mean for security?’ Alexa, Amazon’s virtual assistant, was reported to have accidentally recorded a conversation in May of this year. Even before this happened, my clients were prepared for this possibility, and required employees to disable Alexa before working. If you see a new technology on the market that gives you concerns, don’t be afraid to voice that to leadership, and be quick about updating your policies.
Why is HR so crucial to cyber-security? Besides, of course, their proximity to personal data.
Cyber-security is a huge picture, most departments only see a small piece of it, even the c-suite only sees a fraction. HR is the connector – IT, marketing, leadership, sales, new hires, vendors – and as such, we are uniquely positioned to get the best view.
What can HR do to encourage tech providers to bump up security?
Ask questions of your vendors. Find out how they protect your data, and what will happen if there is a breach. Make sure they know, that as the customer, that you care!
Why data protection now?
Cyber-security wasn’t necessarily a huge deal until we all started hearing about all these high-profile hacks: Target in 2011, Yahoo in 2013, Sony in 2014, Uber in 2016, that brought to light what the power of cyber in the wrong hands could actually do. It’s traumatic! We have to remember, In today’s world, even a mom and pop corner store is responsible for big data.
What’s your take on the Sony hack? What can we learn?
No organization is immune from a cyber attack, and the weakest link in any organization is typically an unsuspecting employee who clicks a link, downloads a file, or replies to a hacker unknowingly. I have heard people say “I’m not dumb enough to be tricked by a cyber attacker,” but cyber attacks are perpetrated on thousands of educated and accomplished individuals each year. Possessing an advanced degree in an area of expertise or years of experience won’t stop a determined hacker, but being cyberSAFE will.